Overview
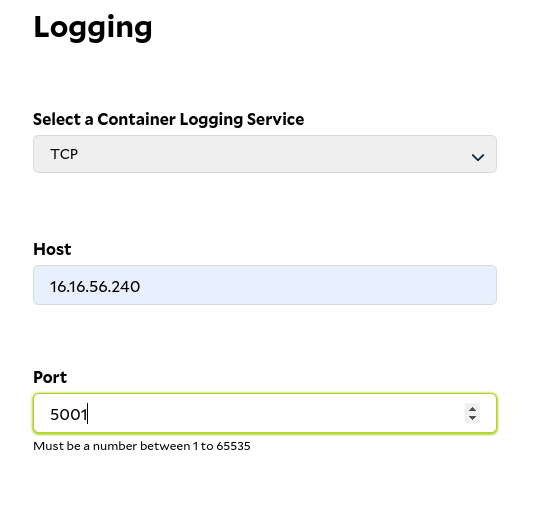
To enable external logging service on SaladCloud , you must configure your Container Group Deployment with the host address and port number of your tcp endpoint. The host should be publicly reachable. Note that all communication between SCE and your TCP endpoint will be encrypted with TLS(Transport Layer Security). Many tools are available to you when creating your TCP endpoint. In this example, we will be using Logstash. Logstash is a free and open-source server-sde data processing pipeline for ingesting and transforming data from a variety of sources.Prerequisite
- Logstash Installation: You must have Logstash installed on the endpoint where you want to receive logs from SCE. To install Logstash, you can follow the official documentation here.
- TLS/SSL Certificates: Prepare SSL/TLS certificates and private keys for securing the communication between Logstash and SCE.
📘 A note on certificates You can use self-signed certificates for testing and development, but in a production environment, it is highly recommended to use certificates from a trusted Certificate Authority (CA).
Generating Self-Signed Certificates
To generate self-signed certificate you can use OpenSSL.- Generate a CA (Certificate Authority) Certificate and Key:
- Generate Logstash Server Certificate and Key:
- Sign the Logstash server CSR with the CA Certificate:
Logstash Configuration
With the certificates ready, it’s time to configure Logstash to accept secure log connections from SCE. Create a Logstash configuration file, typically named logstash.conf, and add the following content:Starting Logstash
Next Steps
Once you’ve set up Logstash, you can configure your Container Group Deployment on SCE and provide the host and port number.