Introduction
JSON Web Token (JWT) is a compact, secure mechanism for authentication and authorization in modern web applications and APIs. It supports stateless authentication, removing the requirement for servers to store session data—ideal for scalable, distributed systems. JWTs can be signed with a private key, and servers verify them using the corresponding public key, ensuring integrity and authenticity. A JSON Web Key (JWK) is a standardized format for representing cryptographic keys in JSON, typically for conveying public keys. A JSON Web Key Set (JWKS) is a collection of JWKs, often used to manage and share public keys for JWT validation. SaladCloud primarily runs GPU-intensive workloads for most use cases, while also requiring interaction with external services or systems to retrieve jobs and return results. Applications can now retrieve JWTs for each Salad node and use the provided JWKS endpoint for JWT-based authentication. This eliminates the need to pass credentials (via environment variables, private images, or other methods) for workloads on SaladCloud to access external services, including cloud providers (AWS, Azure, GCP), as well as custom services (such as Kubernetes and Redis clusters). The solution simplifies identity management, enhances security, and improves scalability. Here are some common scenarios for JWT authentication on SaladCloud:Accessing HTTP Services
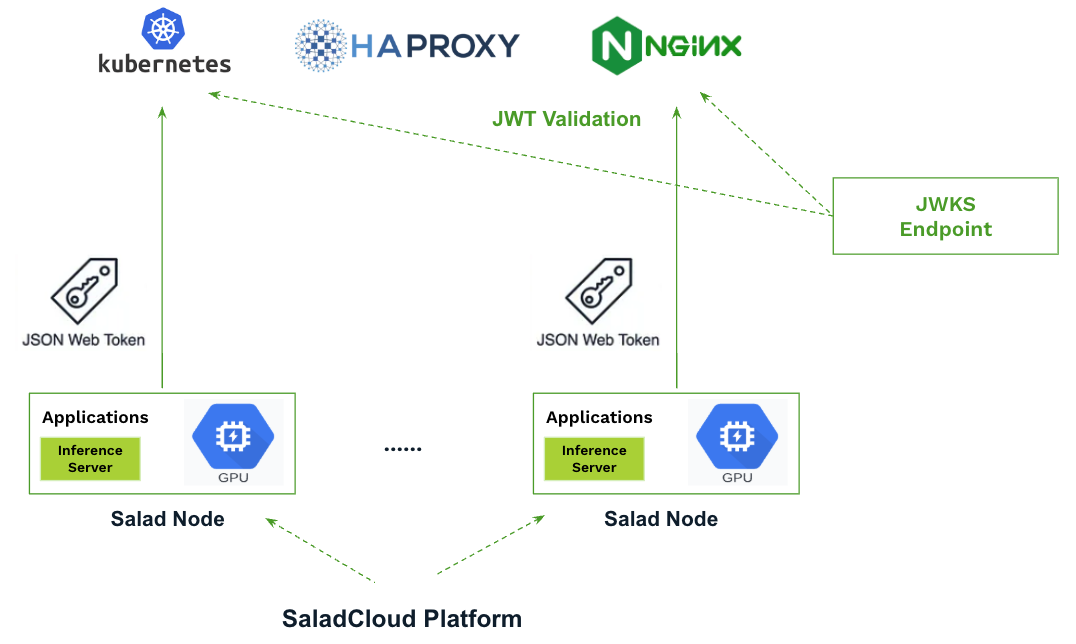
- Applications can obtain the JWT locally on each Salad node and include it in requests to external services, either in the HTTP Authorization header or the request body.
- The services (or proxies) validate the JWT using the JWKS endpoint, granting access and permissions based on the token’s claims, such as salad_container_group_id and salad_machine_id.
Implementing an Identity Broker for Centralized Authentication and Authorization
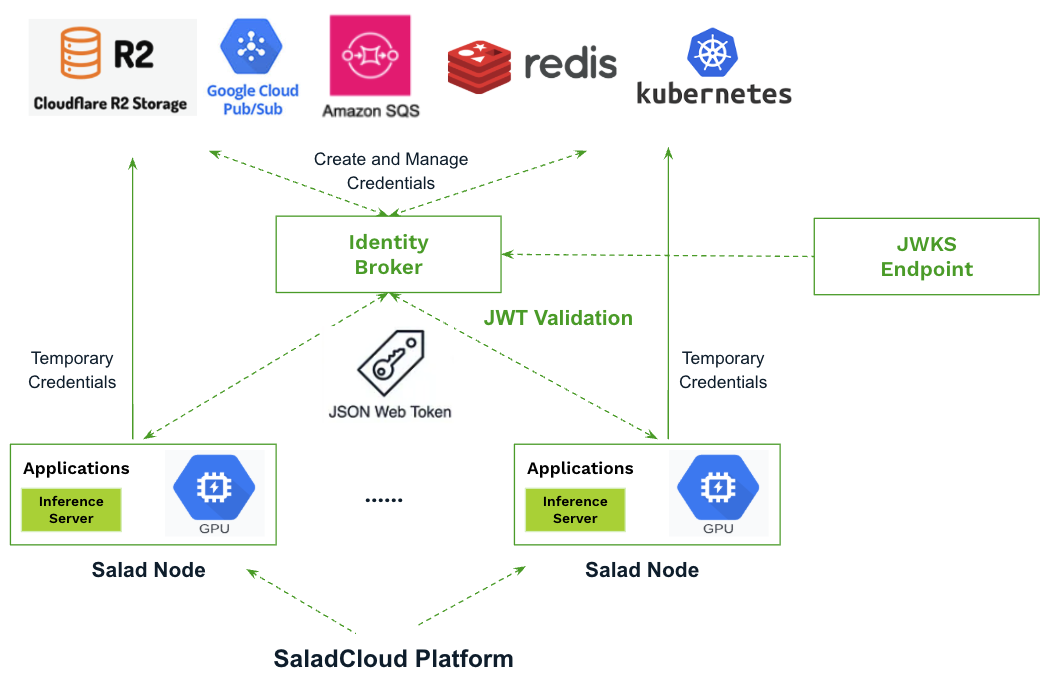
- The identity broker is responsible for creating and managing credentials for external services, including HTTP, TCP, and other protocols.
- Applications on SaladCloud communicate with the broker by including the JWT in their HTTP requests.
- The broker validates the JWT and grants access and permissions (such as API keys, access tokens, or username/passwords) to applications based on the claims within the JWT.
- All sensitive information is encrypted during transit and securely stored in memory on Salad nodes.
JWKS Endpoint on SaladCloud
The JWKS on SaladCloud can be accessed through the JWKS Endpoint. You can retrieve and inspect it using the following command: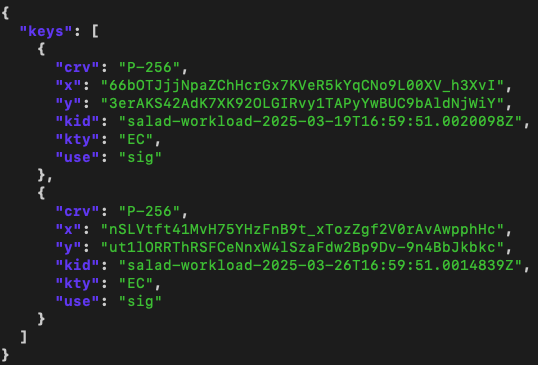
JWT for Salad Nodes
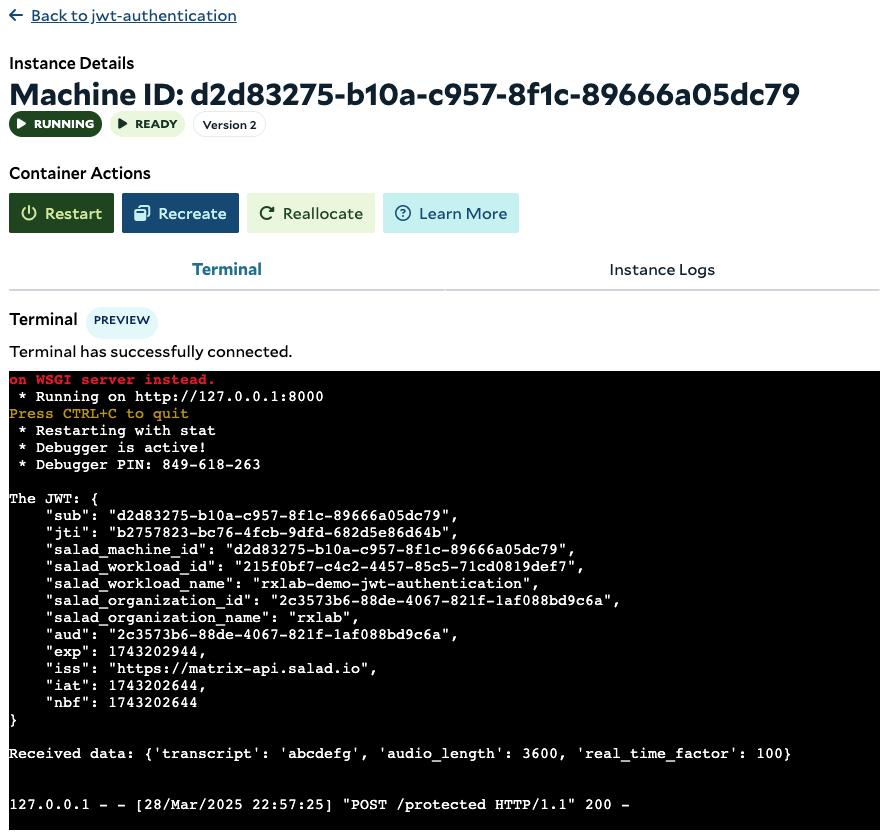
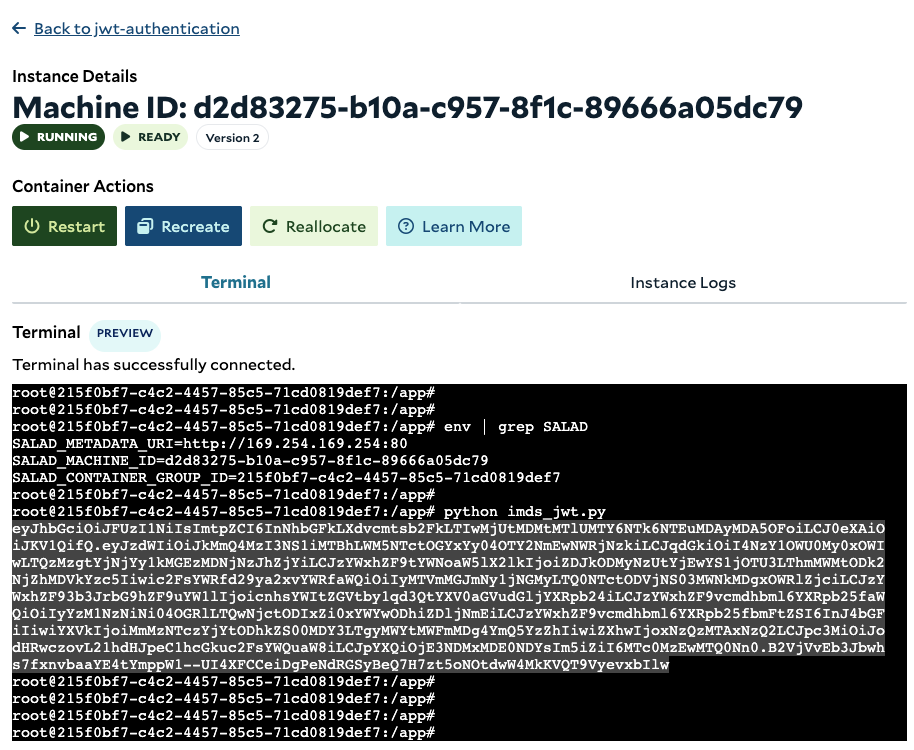
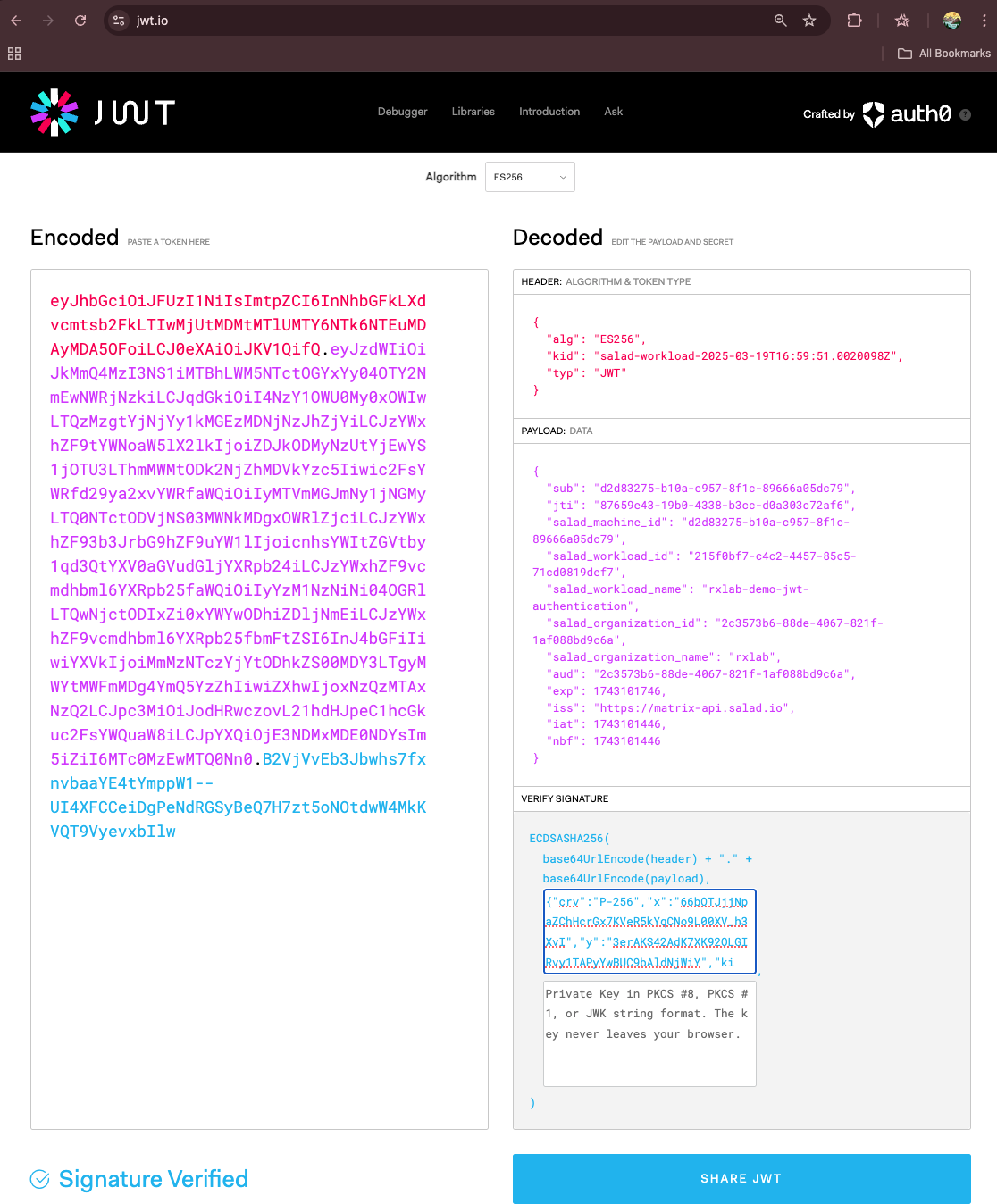
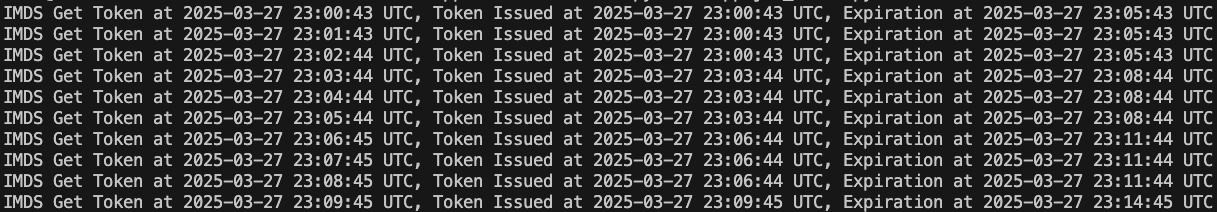
Each Salad node can be issued a JWT that contains essential metadata, including details like salad_machine_id, salad_organization_name, and other relevant information. The JWT expires after 5 minutes, with a new one automatically issued before expiration. The SaladCloud Instance Metadata Service (IMDS) enables applications running on Salad nodes to securely query essential information and manage configurations. The IMDS is available at the non-routable IPv4 address 169.254.169.254 on port 80 of each Salad node, and applications running locally can call the service to check health status, trigger node reallocation, and retrieve the JWT. Note: Applications must bypass any proxies (such as SOCK5 and HTTP) when making requests to the IMDS. Below is an example code of how to retrieve the JWT using the SaladCloud IMDS Python SDK. For more details on obtaining the JWT in different programming languages, please refer to the guide.imds_jwt.py
Build Applications Using JWT Authentication
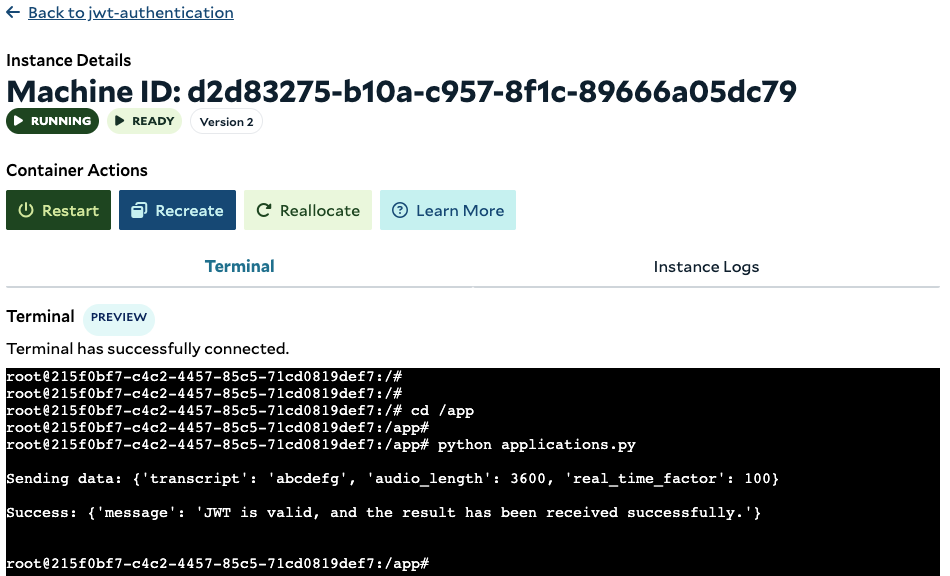
Typically, applications running on Salad nodes obtain the JWT and include it in the HTTP header when making requests to external services. These services validate the JWT against the JWKS endpoint to authorize access or exchange it for fine-grained access to other services. Below are two code snippets: one for applications running on SaladCloud and the other for external services that the applications call to return job results. These examples demonstrate how to use the JWT for authentication. For simplicity, both snippets are executed on a Salad node. Before running the code, ensure that the required Python dependencies are installed, including salad-cloud-imds-sdk, Flask, pyjwt, and cryptography.applications.py
external_services.py