Initial Setup
To get started, follow the quickstart guide to create your Tailscale account and tailnet, then add your first devices (e.g., your developer machine for accessing Salad GPU nodes). You can use either of the interactive methods (Admin Console or CLI with the login process) to join your devices into the tailnet. In the example below, two private, isolated devices are connected via the salad_demo tailnet and can securely communicate with each other.- app-server (Linux): Simulates a private server hosting applications—such as client services, databases, queues, proxies, or identity brokers—that securely interact with Salad nodes over the tailnet.
- dev-vscode (macOS): Represents a developer laptop used for testing, debugging, and managing code running on Salad nodes through the tailnet.
app-server
app-server
Enabling Tailscale SSH
You can install and configure an SSH server on each device, manage authentication using keys or passwords, and enable SSH access between devices within the tailnet using their respective Tailscale IPs. However, Tailscale SSH offers a streamlined alternative by running its own SSH server, which automatically takes over port 22 for connections originating from within the tailnet. It leverages Tailscale keys for authentication and encryption, simplifying access without requiring additional SSH server setup. Additionally, Tailscale SSH can operate seamlessly alongside any existing SSH server, ensuring that non-Tailscale SSH connections to the same host are unaffected.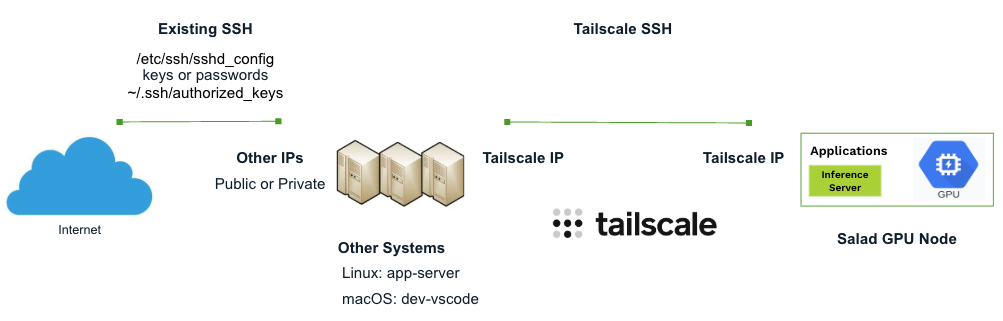
app-server
dev-vscode
app-server
Using Userspace Networking Mode
Tailscale must run in userspace networking mode on Salad nodes, which differs from the default mode. In this mode, Tailscale does not create a virtual network interface. Instead, it provides a local SOCKS5 and HTTP proxy for network communication. Outbound connections to other devices in the tailnet, including other Salad nodes, must be explicitly configured to route through the SOCKS5 or HTTP proxy. In contrast, inbound connections are automatically directed through the SOCKS5 proxy by Tailscale without requiring additional configuration.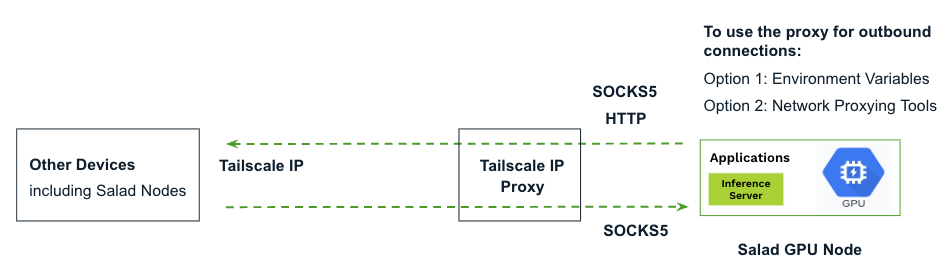
Salad Nodes to others
Salad Nodes to others
- Salad nodes cannot access their own Tailscale IPs directly using any protocols.
- Salad nodes can communicate with each other using TCP and UDP. However, ping does not work due to the use of ICMP; instead, you can use Tailscale ping.
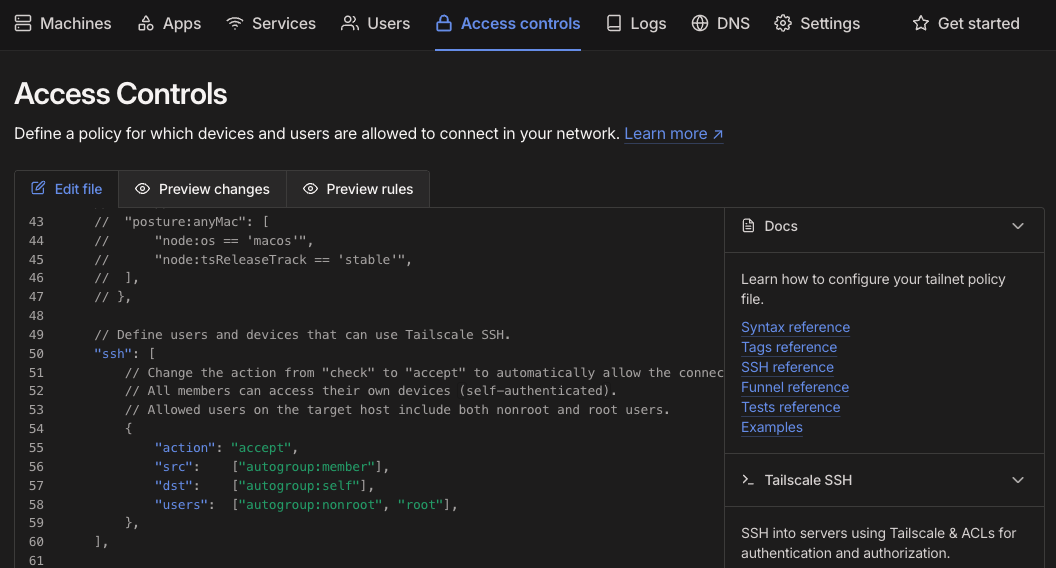
Generating an Auth Key
Auth keys allow you to add devices to a tailnet without requiring interactive sign-in through a browser. They’re especially useful for automated workflows, such as spinning up containers or provisioning devices programmatically. You can generate a reusable and ephemeral key for a group of Salad nodes. The ephemeral option is ideal for short-lived, interruptible devices, like Salad nodes, which typically run for a few hours to several days at a time. Tailscale automatically removes ephemeral devices from the tailnet after 30 minutes to 48 hours of inactivity. If the same device comes online again after removal, it will rejoin the tailnet as a new node. An auth key automatically expires after the duration specified at the time of creation, with a maximum of 90 days (which can be adjusted in the Admin Console). Devices added using the expired key remain authorized, but they will require reauthentication once the configured reauthentication interval has passed.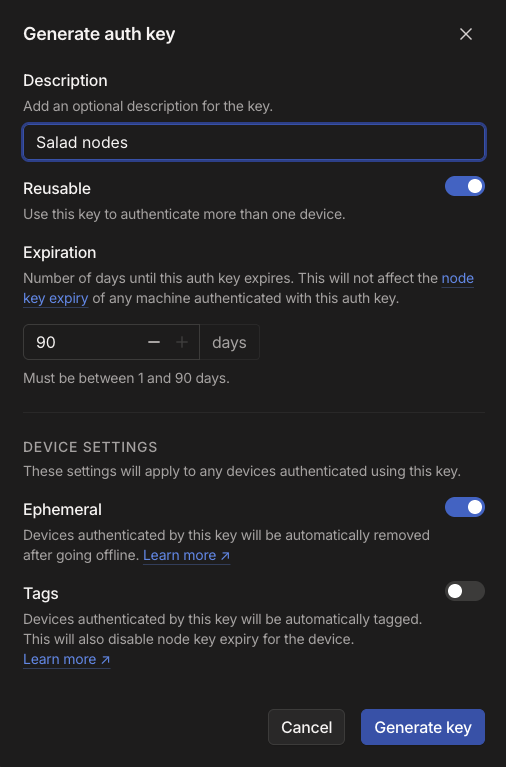
Embedding Tailscale in Container Images
Here is an example application to add Tailscale support for container images running on SaladCloud. The Dockerfile creates a containerized environment by using a base image, then installing essential utilities and required dependencies. It also copies the required Python code and startup script into the image.Dockerfile
- Add the Salad node to the tailnet using a Tailscale auth key and its SALAD_MACHINE_ID, and start the Tailscale SSH server.
- Tailscale IP is retrieved and exported as an environment variable. All environment variables are then written to the /etc/environment file.
- Two applications are launched: a Python Flask web application listening on port 8888 and a JupyterLab instance running on port 8889, both configured with dual-stack support (IPv4 and IPv6).
start.sh
- Tailscale SSH and VSCode Remote - SSH for secure command-line access and seamless code editing and debugging.
- JupyterLab for an interactive data science and notebook experience.
- HTTP requests to interact with the web application, primarily for AI inference tasks.
Deploying SaladCloud Workloads and Joining Them to the Tailnet
Let’s create a container group with the following parameters using the SaladCloud Portal. For deployment using SaladCloud APIs/SDKs, please refer to this link.Removing Inactive Devices Using Tailscale API
All Tailscale accounts support up to 100 devices by default. A device can run Tailscale logout to disconnect from the tailnet and free up the device quota for that node. However, Salad nodes may unexpectedly go down without logging out, and still count toward the quota until Tailscale finally removes them after 30 minutes to 48 hours of inactivity. This temporary period of inactivity may reduce the number of usable devices in the account. You can create a script using Tailscale API to proactively and regularly detect and remove inactive devices after a specified period, such as 5 minutes. This can help maintain an efficient device quota in your account. Please check this example code for more details.Supported Use Cases and Validation
We now have 4 devices connected via the tailnet, including 2 running on SaladCloud:app-server
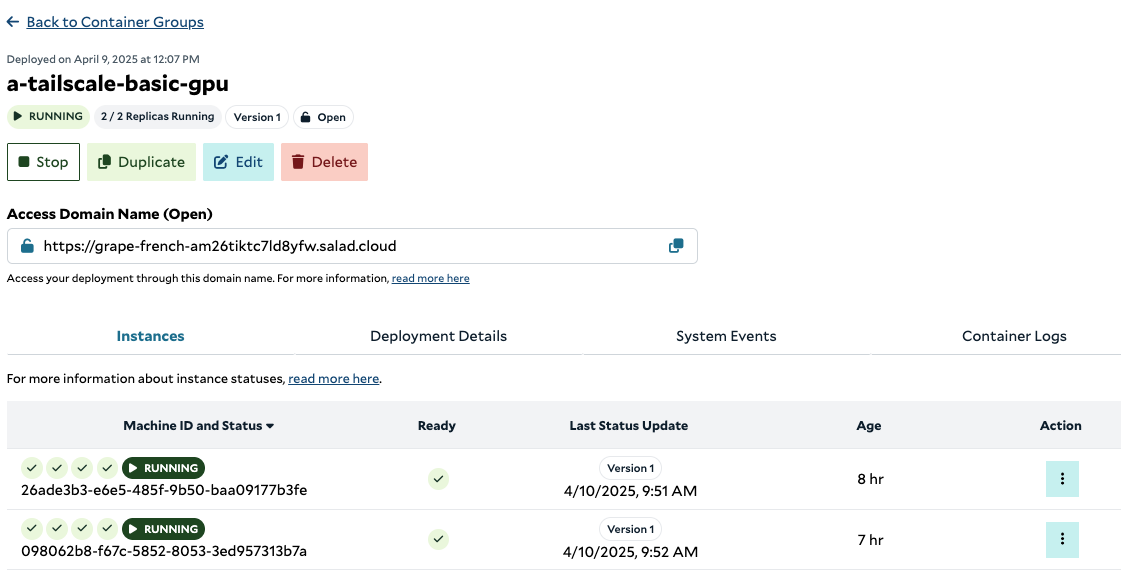
Case 1: Access Salad nodes publicly from Internet via the Container Gateway
Only a single port can be exposed using this method. Client applications can publicly send HTTP requests using the generated access domain name and interact with the backend AI inference services hosted on Salad nodes.Case 2: Access Salad nodes privately via the tailnet
Other systems (such as the app-server and dev-vscode) within the tailnet can access all TCP and UDP-based applications on Salad nodes through CLIs, tools, web browsers, and custom applications.SSH for Network Operators
Network operators can SSH into Salad nodes for configuration, management, and troubleshooting purposes.app-server
VS Code for Developers
AI Developers can use Visual Studio Code Remote - SSH extension to securely access Salad nodes via Tailscale SSH, enabling you to fully leverage VS Code’s development features along with the power of SaladCloud GPUs.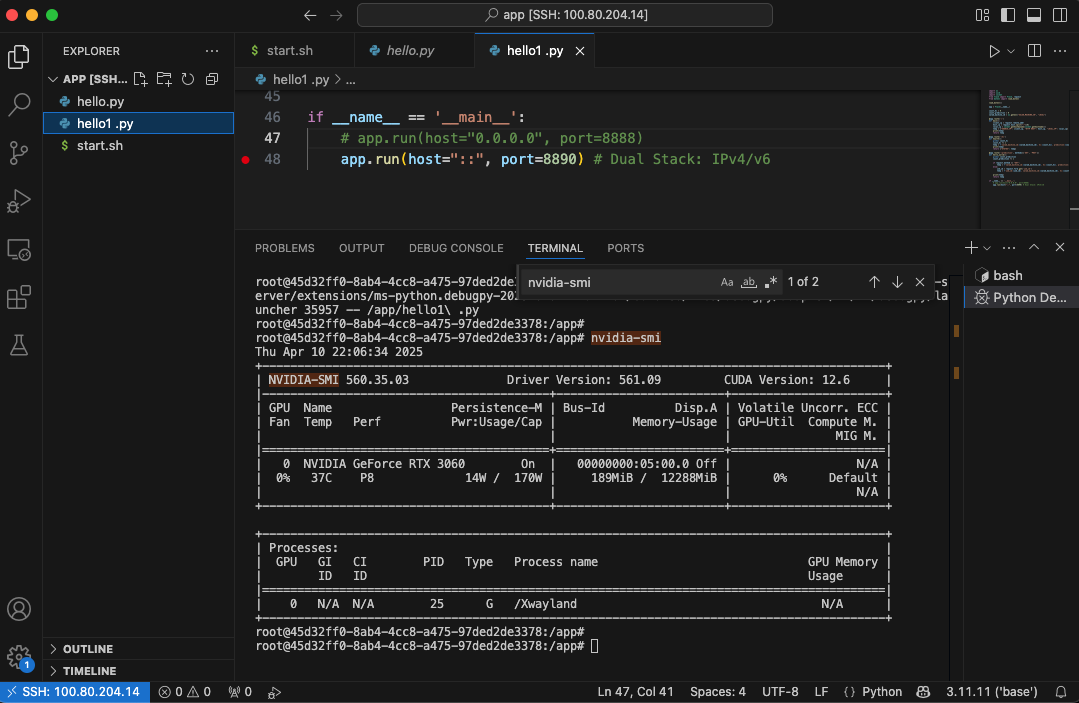
JupyterLab for Data Scientists
Data scientists can use JupyterLab with various GPUs on SaladCloud to explore and analyze data, run machine learning models, and develop data-driven insights efficiently.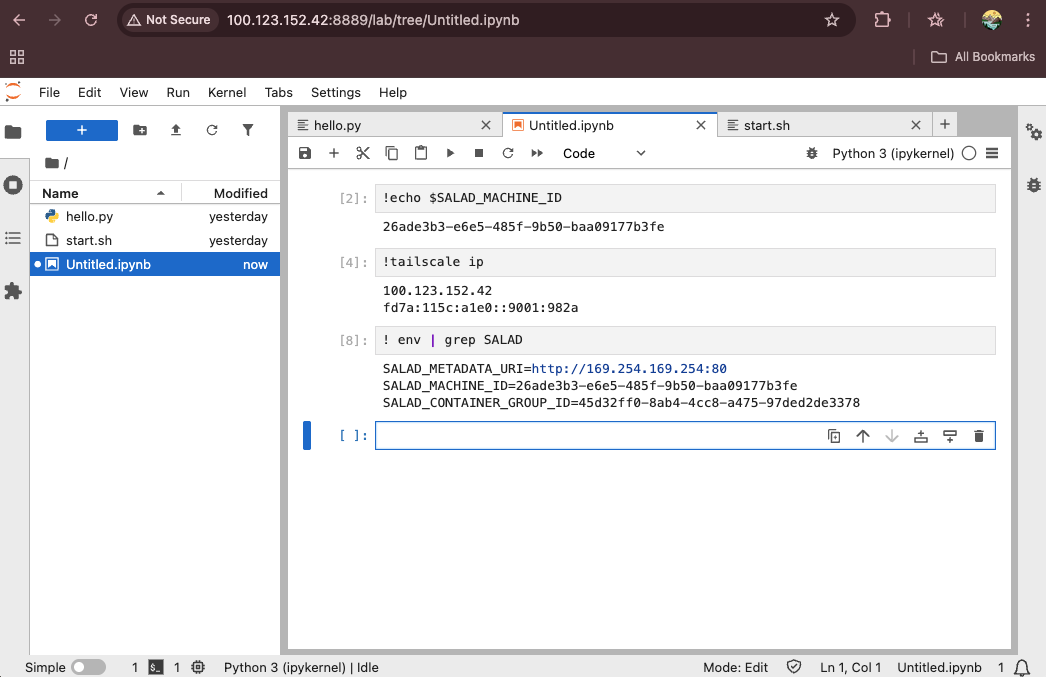
AI Inference for Client Applications
Client applications can privately send HTTP requests to interact with the backend AI inference services hosted on Salad nodes.app-server
Case 3: Salad nodes access other devices privately through the tailnet
Private Connections
Salad nodes can also initiate connections to other systems within the tailnet, such as the app-server (databases, queues, proxies, or identity brokers), ensuring secure and seamless communication. You will need to explicitly configure the environment variables or use network proxying tools to manage outbound connections in this case.Salad Node to Other Systems
Meshed Communication
Salad nodes can communicate with each other, enabling seamless and secure interactions. Similarly, the environment variables or proxy tools must be configured explicitly to manage outbound connections between nodes.Salad Node to Salad Node
Case 4: Salad nodes access Internet publicly
Without using the Tailscale proxy, Salad nodes can still access Internet. This allows them to interact with external services, receiving requests or jobs, and delivering results, while remaining securely connected to the tailnet.Salad Node to Internet